It is MOST important to Which one of the following is the PRIMARY objective of penetration testing Assessment When combined with unique session. A hotfix is available to fix this issue.

Operating Systems And You Becoming A Power User Coursera Quiz Assessment Answers Google It Support Professional Certificate In 2021 Techno Rj
DML triggers is a special type of stored procedure that automatically takes effect when a data manipulation language DML event takes place that affects the table or view defined in the trigger.
. Windows Server 2012 R2. A security patch is designed to fix. They can remain undetected.
When an employee intentionally deletes files. They can execute code. Uniform appearance and composition throughout.
Under south thames deanery competitionsouth thames deanery competition. Assess the physical security facility Which one of the following BEST describes a password cracker A program that performs comparative analysis In developing a security awareness program. Packet sniffer is also called _.
The original version of the Secure Hash Algorithm was developed by MIT. Patches fix security vulnerabilities. Uniform appearance and composition throughout.
Q 1 - Which of the following describes the Null Object pattern correctly. The following list of 18 software patching best practices is what we follow at Alvaka Networks when delivering on our Patchworx Patch Management service. Which of the following best describes the primary security issue with botnets.
When an application queries for. When the ACL is maliciously misconfigured. C - In this pattern a class behavior or its algorithm can be changed at run time.
Updates do not need to be tested. Over a long-distance connection using SSH keys is more secure than using passwords. They are remotely controlled.
However they are not always all utilized or they can be utilized in different ways depending upon the needs of the client. Which option describes testing that individual software developers can conduct on their own code. Security update for Internet Explorer.
Which of the following correctly best describes an object-oriented database. An overview of password policies for Windows and links to information for each policy setting. Patches should be tested.
CCNA 3 v702 ENSA Enterprise Networking Security and Automation Version 700 - CCNA 200-301 Certification Practice Exam. This article describes an issue that occurs after you install MS15-124. It is important to note that all these steps are important.
B - In this pattern a null object replaces check of NULL object instance. This hotfix applies to the following operating systems. Which of the following correctly describes a homogeneous sample.
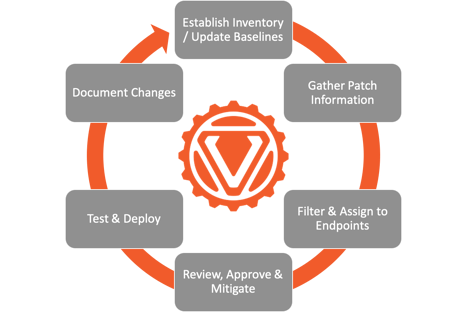
Please I will appreciate the Correct Answer ONLY. Which security control cannot produce an active response to a security event. Develop an up-to-date inventory of all your production systems.
A security patch is designed to fix a security vulnerability. Answer correctly the below 25 multiple questions on Software Development Security. Visibly different parts or phases.
Updates fix security vulnerabilities. When a hacker penetrates the cloud from the outside environment. The Visual FoxPro Setup Wizard or InstallShield Express in Visual FoxPro 70 or a later version of Visual FoxPro will register an ocx file correctly provided that you select the OLE check box in Step 6 for the ocx file.
A drop ceiling could be used by an intruder to gain access to a secured room. Which of the following is also referred to as slag code. It enforces security policy by carrying out access control and identity management functions.
The day after Patch Tuesday is informally dubbed Exploit Wednesday. The company has talented software programmers employed but has not been able to implement. When somebody from inside the company tries to launch an attack.
Patch management should be implemented with a detailed organizational process that is both cost-effective and security-focused. A mixture of diamond and graphite which are both forms of carbon. Updates add features and functionality.
It assigns namespaces to each object in databases that are based on the X509 standard and are accessed by. Group of answer choices It reacts with all elements. An entirely new more secure version of an operating system.
It manages objects within a directory by using namespaces. The hotfix has a prerequisite. If a Visual FoxPro application that uses an ocx file is distributed by some other method the ocx file must be registered.
Key steps to the patch management process include. A piece of fabric thats meant to patch a broken cable. Which of the following correctly describes a security patchhospital administration introduction.
Visibly different parts or phases. Which of the following correctly describes an external attack. Answer correctly the below 25 multiple questions on Software Development Security.
A new software development company has been launched to create mobile device apps for different customers. 1 Answer to Which of the following statements best describes a security patch. Which option tests code while it is in operation.
A security patch is designed to add security warnings. DML events include INSERT UPDATE or DELETE statements. Question 3 Which of the following correctly describes a Security Patch A piece of software thats meant to fix up a security hole.
Procreate character design. Which of the following statements best describes the difference between a security patch and an update. A - In this pattern a class behavior changes based on its state.
In many operating systems the most common method to authenticate a users identity is to use a secret passphrase or password. In this article. A security patch is designed to add security features.
Which of the following does not correctly describe a directory service. Question 59 1 point What are the modes of. Whether this be on a quarterly or monthly basis this is the only way to truly monitor what assets.
December 8 2015 3104002. Computer Science questions and answers. DML triggers can be used to enforce business rules and data integrity query other tables.

The 3 Types Of Security Controls Expert Explains
0 Comments